The Security/Command Permissions Subtab
The Command Permissions subtab of the Security tab displays the set of rules governing which users are allowed to execute a variety of administrative-level commands. Configuring these rules in the Command Permissions subtab provides an alternative to writing Perl script in the server_admin_trig.bat or server_admin_trig.pl files installed in the <ac-install>/storage/site_slice/triggers directory.
Opening a Security/Command Permissions Subtab
Choose Admin > Security from the GUI main menu to display the Security tab. Then, click the Command Permissions subtab.
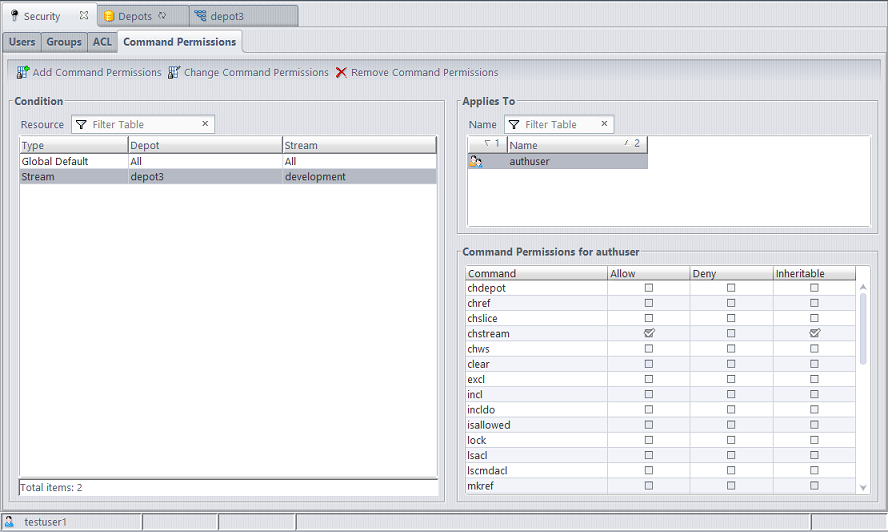
Security/Command Permissions Subtab Layout
The Command Permissions subtab contains three panels: Condition, Applies To, and Command Permissions.
The Condition panel contains a table with the following columns:
|
Type |
The type of resource to which the command permissions apply: Global Default or Stream. Global Default allows you to configure admin command permissions for the entire site. Stream allows you to configure stream-related command permissions for a particular stream or stream hierarchy. |
|
Depot |
A depot name, or All if Type is Global Default. |
|
Stream |
A stream name, or All if Type is Global Default. The stream or the base of the stream hierarchy to which command permissions apply. |
The Applies To panel contains a table with the following columns:
|
(icon) |
An icon that indicates whether the named principal is a user or a group. |
|
Name |
The name of the AccuRev user or group whose command permissions are specified. authuser denotes all users that have a password; anyuser denotes all users that do not have a password. |
The Command Permissions panel contains a table with the following columns:
|
Command |
The name of an AccuRev command. Only stream-related commands are listed if a stream resource is selected in the Condition panel. |
|
Allow |
If Allow is selected for a command, the user or group selected in the Applies To table is allowed to execute that command in the stream that is selected in the Condition table. |
|
Deny |
If Deny is selected for a command, the user or group selected in the Applies To table is not allowed to execute that command in the stream that is selected in the Condition table. |
|
Inheritable |
(The Inheritable column is visible only for conditions applying to a stream.) If selected, the command permission applies to the entire stream hierarchy rooted at the selected stream. If cleared, the command permission applies only to the selected stream. |
Working in a Security/Command Permissions Subtab
You can use the Command Permissions subtab to allow or deny permission to certain users or groups to perform selected commands on specific streams.
In order to set or remove admin command permissions, you must either be a superuser or have been granted explicit “allow” permission for the setcmdacl and rmcmdacl commands. To designate a user as the superuser, the AccuRev administrator must use the maintain utility:
maintain su -a <username>
Changing Command Permissions
To edit command permissions, you can either add a new condition or select an existing condition to change. The conditions are either the site-wide “Global Default” command permissions or command permissions set on a specific stream. Only commands that apply to a stream or stream hierarchy can be configured at the stream level. Examples of commands that are configurable by stream are: setting stream properties, mkstream, and chstream.
Do one of the following to edit a condition:
- Double-click on the condition.
- Click on the condition and then click the Change Command Permissions button.
- Right-click on the condition and choose “Change Command Permissions” in the context menu.
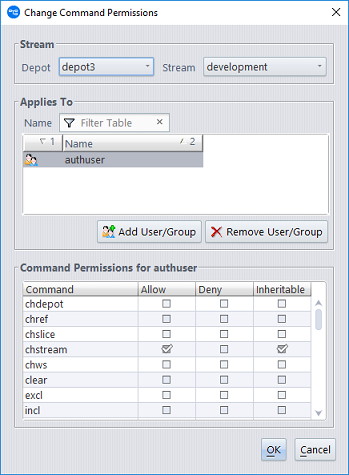
The following dialog will appear:
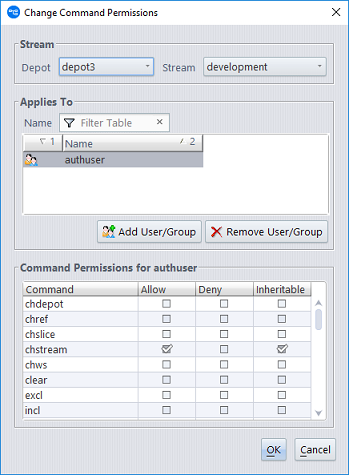
Use the Add User/Group and Remove User/Group buttons to specify the users and groups whose command permissions you want to configure. Command permissions are configured for a single user or a specific group of users at a time. This is similar to how Windows file permissions can be configured. You can add multiple users to the Applies To section of the dialog, but the Command Permissions that you configure apply only to the currently highlighted user or group. The title of the Command Permissions section identifies the user or group whose permissions are being configured.
Once you have configured permissions for the desired set of users and groups, click OK to save your changes.
Stream-Aware Command Permissions
For commands that apply to a stream or stream hierarchy, you can add a condition for that stream and configure command permissions that you want to apply only to that stream. You can also make your command permission setting inheritable so that it applies to the entire stream hierarchy below the specified stream.
For example, suppose you want to allow users to change the streams in the "development" stream hierarchy, but you don’t want anyone to change streams above that level. To accomplish this, you could deny access to chstream in the global default, but set an explicit inheritable "allow" permission for the chstream command on the “development” stream.
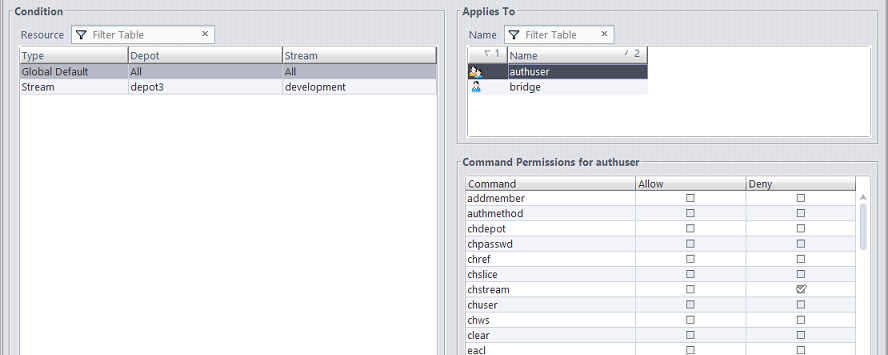
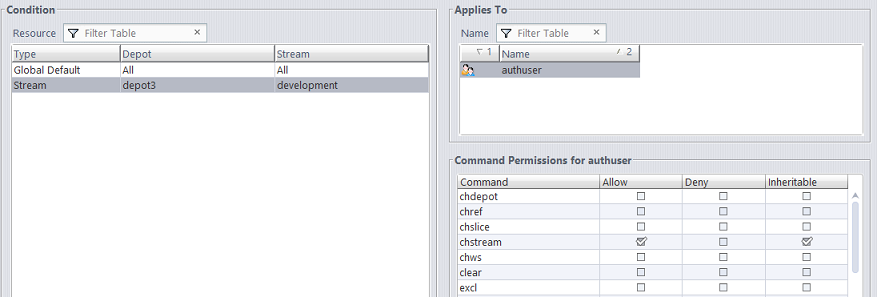
Conflicting Permissions
If permissions have been configured for both a user directly and a group which the user is a member of, the permission setting closest to the user is the one that applies. For example, if a user is a member of the “qa” group and the “qa” group is denied access to the chstream command, but the user is specifically configured to be allowed permission to the chstream command, the user’s own permission is the one that applies.
Removing Command Permissions
To remove a condition entirely (aside from the Global Default Condition, which is not removable), highlight the condition and click the Remove Command Permissions button.
To remove command permissions from a condition for a specific user or group, highlight the condition and click on Change Command Permissions. In the dialog that opens, remove the users and groups that you no longer want permissions to be set for.
By default, if no permission is set for a user, for any group they are a member of, or for the built-in group that they belong to (authuser or anyuser), then the user is implicitly granted "allow" permission for that command.










