| Field (*Required) |
Description |
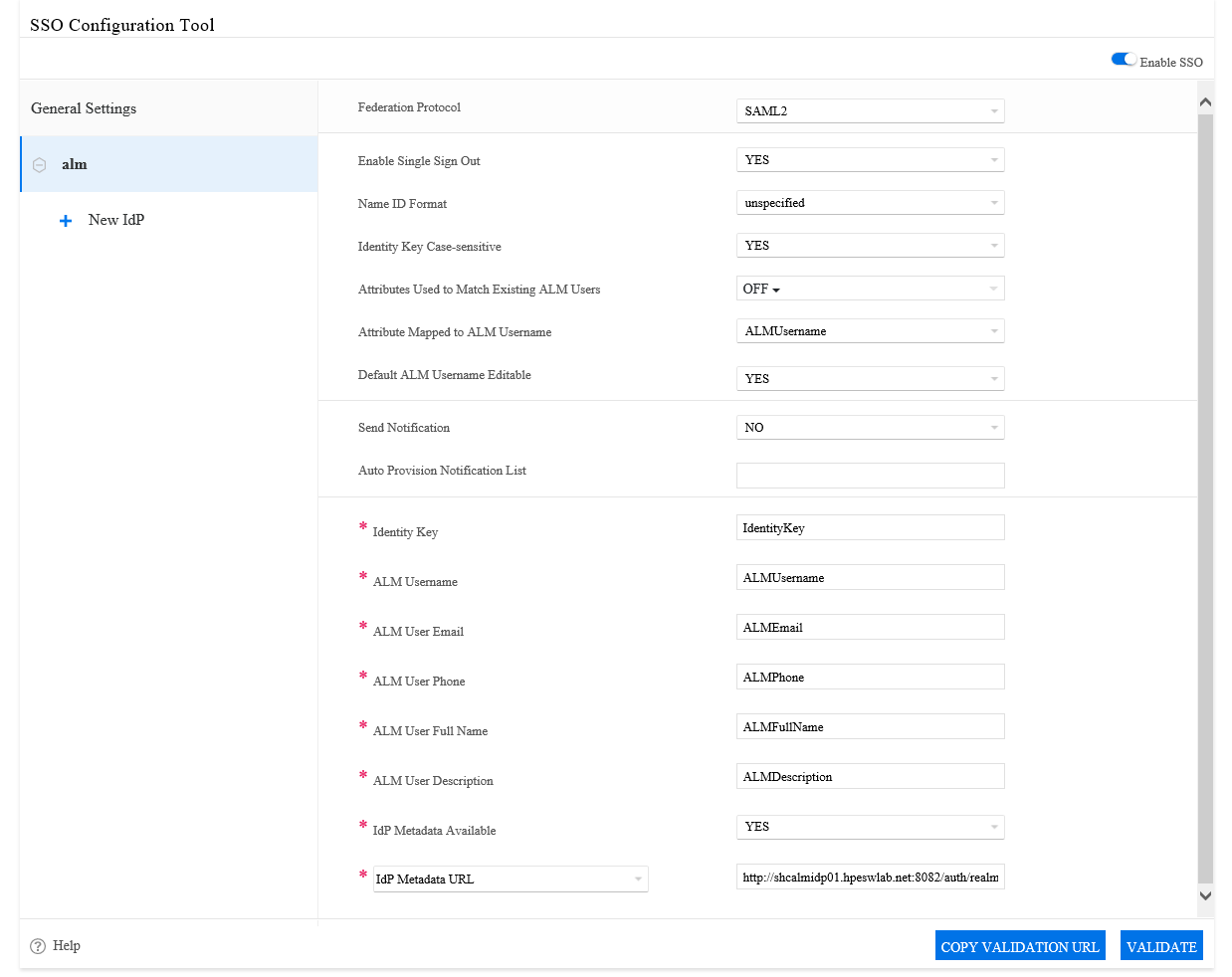
| Protocol configuration |
|
Federation
Protocol
|
Select
the federation protocol (SAML2 or OIDC) that ALM will use to
communicate with IdPs.
The OIDC protocol requires that the ALM Server should establish network connections with the IdP.
|
|
OpenID
Issuer
OpenID
Client ID
OpenID
Client Secret
|
Provide
the issuer, client ID, and client secret. They are specified when you create a client that uses OIDC as the protocol in the IdP.
They are available and required only when you select OIDC as the federation protocol.
|
|
Single sign out configuration
|
|
Enable
Single Sign Out
|
This option controls whether or not the ALM supports
single sign out. It is available only when you select SAML2 as the federation
protocol.
If you change the value of this option after enabling SSO, you should restart the ALM Server to make your change take effect.
|
| Name ID Format |
Name ID format supported by the IdP.
Only available when you select SAML2 as the federation
protocol.
|
| Identity Key Case-sensitive |
When ALM authorizes IdP users with identity keys, whether or not ALM treats the letters in the identity keys as case-sensitive.
- Yes: case-sensitive
- No: case-insensitive
|
|
Auto user-provisioning configurations
|
|
Attributes Used to Match Existing ALM Users
|
If, after authenticating an IdP user, ALM fails to find a matching ALM user for the user
based on the Identity key and IdP ID, this option controls the following:
- whether or not to enable user
auto-provisioning to find a matching user in ALM using other attributes.
-
if auto user-provisioning is enabled to find the matching ALM user, then which attributes ALM will use to
find the matching user and then attach the Identity Key and IdP ID
information of the IdP user to the matching ALM user.
OFF: Disable
auto user-provisioning to find matching ALM users.
Other selected
values: Enable auto user-provisioning to find matching ALM users.
- ALM will use the first selected attribute to find the matching
user, if only one matching user is found, then the Identity Key and Identity
ID information is attached to the user;
- If more than one matching user is
found, then ALM will continue to filter the matching users using the second
selected attribute, and the process goes on until only one matching user is
found.
- If ALM fails to find only one matching user after filtering users by all the selected attributes, ALM will check whether auto user-provisioning is enabled to create users for the IdP user.
|
|
Attribute
Mapped to ALM Username
|
If ALM fails to find the only one matching ALM user for an IdP user
based on the Identity key and IdP ID and other specified attributes, this
option controls the following:
- whether or not to enable auto user-provisioning to create a matching
user in ALM for the IdP user.
-
if auto user-provisioning is enable to create a user, then which attribute ALM will use as the default username when
creating the user.
OFF:
Disable auto user-provisioning to create users.
IdentityKey:
When creating new users, ALM will use the IdentityKey value as the new ALM username.
ALMUsername:
When creating new users, ALM will use the ALMUsername value as the new ALM username.
ALMEmail:
When creating new users, ALM will use the ALMEmail value as the new ALM username.
|
|
Default
ALM Username Editable
|
Whether
or not the new ALM user can change its default username during user creation.
Its value is disregarded if the option Attribute
Mapped to ALM Username is set to OFF.
|
|
Email notification configurations
|
|
Send
Notification
|
This
option controls whether or not to send email notification to the related
users in the following circumstances:
- When new users are created during auto user-provisioning, this
option controls whether or not to
send notification to the new users and the site admin users.
- When an IdP user accesses the copied SSO validation URL to validate SSO
authentication, this option controls whether or not to send notification to
the site admin users.
|
|
Auto
Provision Notification List
|
If
email notification is enabled, provide the usernames of the notification receivers in
this field. Separate usernames with semicolons.
|
|
IdP user attributes mapping
|
|
*Identity
Key
|
Enter
the IdP user attribute mapped to the ALM user attribute IdentityKey.
|
|
*ALM
Username
|
Enter
the IdP user attribute mapped to the ALM user attribute ALMUsername.
|
|
*ALM
User Email
|
Enter
the IdP user attribute mapped to the ALM user attribute ALMEmail.
|
|
*ALM
User Phone
|
Enter
the IdP user attribute mapped to the ALM user attribute ALMPhone.
|
|
*ALM
User Full Name
|
Enter
the IdP user attribute mapped to the ALM user attribute ALMFullName.
|
|
*ALM
User Description
|
Enter
the IdP user attribute mapped to the ALM user attribute ALMDescription.
|
|
Share IdP metadata with ALM SP
|
|
IdP Metadata Available
|
Whether or not the real IdP metadata is available to be
shared with ALM SP. It is required only when you select SAML2 as the
federation protocol.
-
NO: Select NO if you have not obtained the IdP
metadata yet. ALM will provide a temporary mock IdP metadata to the SP so
that ALM can start service and load the SP metadata.
Once you obtain the real IdP metadata, you should change
the value to YES, provide the metadata with a URL or XML text, and restart the ALM server.
-
YES: Select YES if you have already obtained the
IdP metadata. Provide the metadata with a URL or XML text.
-
IdP Metadata:
Plain-text XML of the SAML metadata descriptor from the IdP. This should
be used if the IdP metadata URL cannot be accessed from the ALM server.
-
IdP Metadata URL:
The IdP’s URL for publishing IdP metadata. Choose this if the IdP metadata
URL can be accessed by the ALM server.
|
 Next steps:
Next steps: 














