Business Environment
In the Business Environment section, enter the critical business properties of the application.
All users can view the data in this section. Users assigned one or more of the following roles can edit the data in this section: Business Owner, Technical Owner, or Respondent (when more information is requested).
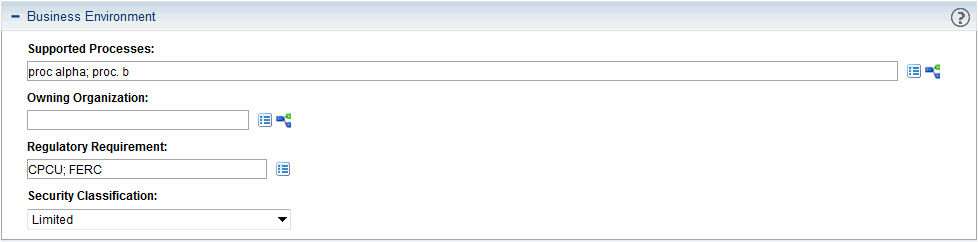
Figure A-3. Application Business Environment section
|
Field |
Description |
|---|---|
|
Supported Processes |
Zero, one, or more business processes that are supported by the application. |
|
Owning Organization |
The name of the organization with business ownership of the application.Organization units are created in Project and Portfolio Management Center (PPM). (For instructions for creating organization units, see the Resource Management User Guide.) |
|
Regulatory Requirement |
Zero, one, or more compliance requirements for the application.
|
|
Security Classification |
The highest security level designated for the components of this application. That is, if the components of this application have different security classifications, select the highest classification.
|











