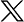Overview of Program Management configuration
This section presents information about the high-level steps involved in configuring Program Management for your organization. Configuring Program Management Request Types and Workflows and Configuring Security for Program Management contain the detailed procedures you use to perform these steps.
Step One: Gather Information
The first step in configuring Program Management is to gather your program requirements. To deploy Program Management effectively, you must determine which program-related request types to use.
Different kinds of information are required to process each program-related request. For each field in the program-related request, collect the following information:
-
Field name. Field names help ensure that the information captured in a request is correct and sufficient. Use the Request Type Workbench to set up a request so that it contains the fields required to gather the required information.
-
Information type. What type of information do you need? Should the value of the field be entered as text, or will users select a value from a list? The field information type is governed by its validation, which defines the field component type, as well as what information users can enter in the field. For example, a field using a numeric text field validation accepts only numeric values.
-
Field behavior. Configuring the behavior of a field helps to ensure that the correct information is collected. For example, to ensure that requests include specific information, you can make a field required.
You can set up fields that are populated automatically based on values in other fields. You can also set up fields that are read-only or hidden based on the access grants or the workflow step.
Note: For detailed information about how to configure request types, see the Demand Management Configuration Guide.
Table 1-2. Program Management request types and workflows lists the request types and workflows that are supplied for all Program Management entities.
If these request types and workflows are adequate, no further requirements gathering is necessary.
Note: For information on how to add Program Management-related portlets to PPM Dashboard pages, see the Creating Portlets and Modules guide. For information on how to add the preconfigured Program Manager page to the PPM Dashboard and modify it to suit your needs, see the Program Management User Guide.
Step Two: Configure Program Management Request Types
After you gather program requirements, configure the request header types associated with existing request types to include the required Program Management field group. For details, see Configuring Program Management Request Types and Workflows.
Note: Field groups are sets of preconfigured fields delivered with PPM. You can use them to implement a solution quickly or to enable certain functions simultaneously. For example, in Demand Management, the Demand Management Scheduling Fields field group enables consistent tracking of information across multiple request types.
Step Three: Configure Program Management Workflows
Configure the request header types associated with workflows to include the required Program Management field group. For details, see Configuring Program Management Workflows.
Step Four: Add Custom User Data Fields to Program Pages
You can define custom fields to capture additional information that standard fields on the View Program and Modify Program pages in the PPM Dashboard do not capture. For information on how to create custom user data fields, see Configuring User Data.
Step Five: Set Security for Program Management
Businesses often control access to certain information and business processes to protect sensitive information such as employee salaries, or to simplify business processes by hiding data that is irrelevant to specific users. PPM includes features to help control data and process security by letting you:
-
Select program managers and set up security access grants for these resources
-
Determine who is to report on issues, risks, and scope changes, reporter and set up security access grants for these resources
-
Limit the data displayed in some fields or windows
-
Specify who can view, create, edit, or process PPM entities such as requests, packages, projects, portfolios, and programs
-
Specify who can view, create, or edit PPM configuration entities such as workflows, request types, object types, and security groups
-
Specify who can change security settings
Note: In addition to the security-related tasks described in this guide, the program manager can use the Control Access page to configure security for a specific program. For details on how to use the Control Access page, see the Program Management User Guide.
The steps you perform to configure security groups and users for Program Management are described in Configuring Security for Program Management.
Note: Some business models require that specially designated security administrators set up user access grants and restrictions.