Set Message Security
This task describes how to configure settings for the default message security modes.
Note:
- This task is part of a higher-level task. For details, see Set Security.
- To learn more about OpenText Service Virtualization security, see Virtual service security.
In the Virtual Service Editor, under Security Settings, configure one of the following security modes for your virtual service.
Configure CertificateOverTransport mode
Certificate over transport mode uses an endorsing supporting binary token over HTTPS:
-
Transport security binding
- Algorithm suite: Basic256
-
Layout: Strict
-
Endorsing supporting token
- X509Token (WssX509V3Token10) always included to recipient
- Inclusion type: MustSupportRefThumbprint / RequireThumbprintReference
To configure CertificateOverTransport mode:
-
Prerequisites:
- You must have created a virtual service.
- The OpenText Service Virtualization Credential Store must contain an identity with each used client certificate.
- Certificates must contain a private key.
- In the Virtual Service Editor, expand Security Settings. Under Message Security, select Enabled.
-
In the Mode drop-down box, select CertificateOverTransport.
Note: Do not configure Real Service Identity or Virtual Service Identity
-
Click Advanced Settings to open the Advanced Message Security Settings dialog box, and configure as follows:
- Protection Level. This setting has no effect because encryption and signing are provided by the transport level (HTTPS).
- Message Protection Order. This setting has no effect because encryption and signing are provided by the transport level (HTTPS).
- Message Security Version. Only WS-Security 1.1 is supported because this configuration mode requires thumbprint token inclusion mode which is not supported in WS-Security 1.0.
- Require Derived Keys. This setting should not be changed.
- Include Timestamp. This setting must be checked because the endorsing supporting token passed in the request must sign the timestamp header.
- Allow Serialized Signing Token on Reply. This setting has no effect.
Configure DigestPasswordAndUserNameOverTransport mode
Requires a username security token within the request message and forwards the token into the outgoing request to a real service during Learning and Standby modes. It ignores the response message, leaving any token (if present) to be learned as part of the response. During simulation, learned response tokens are used.
Example of the request security header containing the username token:
Example: <o:Security s:mustUnderstand="1" xmlns:o="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<wsse:UsernameToken wsu:Id="uuid-c7f6a73a-6da9-479c-8383-f9ae4766e1a3-26" xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsse:Username>requestSample</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordDigest">opF+QBL2BzrO9+H7CPcp3XF1uro=</wsse:Password>
<wsse:Nonce>aLtQ7CsnEdssRz+PrqN4Vw==</wsse:Nonce>
<wsu:Created>2015-05-25T11:38:21Z</wsu:Created>
</wsse:UsernameToken>
</o:Security>
To configure DigestPasswordAndUserNameOverTransport mode:
-
Prerequisites:
- You must have created a virtual service.
- The OpenText Service Virtualization Credential Store must contain an identity with each used client certificate.
- Certificates must contain a private key.
- In the Virtual Service Editor, expand Security Settings. Under Message Security, select Enabled.
-
In the Mode drop-down box, select DigestPasswordAndUserNameOverTransport.
Note: Do not configure Real Service Identity, Virtual Service Identity, or Security Applied To.
Configure MutualCertificate mode
MutualCertificate is a mode with asymmetric security binding (WS-Security 1.0) which uses both client and server certificates to secure messages over unsecured transport (HTTP):
-
Asymmetric security binding
- Initiator token: X509Token (WssX509V3Token10) always included to recipient.
- Recipient token: X509Token (WssX509V3Token10) never included.
- Algorithm suite: Basic256
- Layout: Strict
-
Token inclusion type:
- MustSupportRefKeyIdentifier
- MustSupportRefIssueSerial
To configure MutualCertificate mode:
-
Prerequisites:
- You must have created a virtual service.
-
The OpenText Service Virtualization Credential Store must contain an identity with a real service certificate.
If the certificate does not contain a private key, the Credential Store must also contain an identity for the virtual service, with a certificate containing a private key.
- The Credential Store must contain an identity with each used client certificate.
- Client certificates must contain a private key.
- In the Virtual Service Editor, expand Security Settings. Under Message Security, select Enabled.
-
In the Mode drop-down box, select MutualCertificate.
-
In the Real Service Identity drop-down box, select an identity configured in the Credential Store.
If the identity for the real service does not contain a certificate with a private key, or if you want to use separate identity for the virtual service, select an identity configured in the Credential Store for Virtual Service Identity. This identity must contain a certificate with a private key.
-
Click Advanced Settings to open the Advanced Message Security Settings dialog box, and configure as follows:
- Protection Level. Configures the level of security applied to each message.
- Message Protection Order. Configures the order of protection operations used to secure messages.
-
Message Security Version. Use only WS-Security 1.0.
- Require Derived Keys. This setting should not be changed.
- Include Timestamp. This setting controls if requests and responses must contain a security timestamp.
- Allow Serialized Signing Token on Reply. This setting has no effect.
Configure MutualCertificateDuplex mode
MutualCertificateDuplex mode with asymmetric security binding (WS-Security 1.0 and 1.1) uses both client and server certificates to secure messages over unsecured transport (HTTP). The difference between MutualCertificate and MutualCertificateDuplex is that MutualCertificateDuplex security mode also sends the recipient’s signing token back to the initiator.
-
Asymmetric security binding
-
Initiator token: X509Token (WssX509V3Token10) always included to recipient.
-
Recipient token: X509Token (WssX509V3Token10) always included to initiator.
-
Algorithm suite: Basic256
-
Layout: Strict
-
Token inclusion type depends on WS-Security version configured in Advanced settings::
-
WS-Security 1.0
- MustSupportRefKeyIdentifier
- MustSupportRefIssueSerial
-
WS-Security 1.1
- MustSupportRefThumbprint / RequireThumbprintReference
-
-
To configure MutualCertificateDuplex mode:
-
Prerequisites:
- You must have created a virtual service.
-
The OpenText Service Virtualization Credential Store must contain an identity with a real service certificate.
If the certificate does not contain a private key, the Credential Store must also contain an identity for the virtual service, with a certificate containing a private key.
- The Credential Store must contain an identity with each used client certificate.
- Client certificates must contain a private key.
- In the Virtual Service Editor, expand Security Settings. Under Message Security, select Enabled.
-
In the Mode drop-down box, select MutualCertificateDuplex.
-
In the Real Service Identity drop-down box, select an identity configured in the Credential Store.
If the identity for the real service does not contain a certificate with a private key, or if you want to use separate identity for the virtual service, select an identity configured in the Credential Store for Virtual Service Identity. This identity must contain a certificate with a private key.
-
Click Advanced Settings to open the Advanced Message Security Settings dialog box, and configure as follows:
- Protection Level. Configures the level of security applied to each message.
- Message Protection Order. Configures the order of protection operations used to secure messages.
-
Message Security Version. this setting defines how the binary token is referenced in the request message.
- Message security versions using WS-Security 1.0 requires either issuer serial number or key identifier of the certificate.
- Message security versions using WS-Security 1.1 requires thumbprint of the certificate.
- Require Derived Keys. This setting should not be changed.
- Include Timestamp. This setting controls if requests and responses must contain a security timestamp.
- Allow Serialized Signing Token on Reply. You must select this setting because the recipient’s signing token is always send back to an initiator.
Configure SignOnlyWithMutualCertificate mode
Requires a message body signature, optionally signed headers, and an X509 security token within the incoming request or response message. Adds a body and SOAP headers signature and an X509 security token into the generated request and response messages.
-
Prerequisites:
- You must have created a virtual service.
- The OpenText Service Virtualization Credential Store must contain an identity with each used client certificate.
- Certificates must contain a private key.
- In the Virtual Service Editor, expand Security Settings. Under Message Security, select Enabled.
-
In the Mode drop-down box, select SignOnlyWithMutualCertificate.
-
In the Virtual Service Identity drop-down box, select an identity configured in the Credential Store. The certificate within the request message must match the certificate of the identity.
-
In the Security Applied To drop-down box, select which message parts to apply the security to - request, response, or both.
Note: Do not configure Real Service Identity.
Configure EncryptOnlyWithMutualCertificate mode
This configuration implements WS-Security encryption of the body element and the Username Token security header.
Messages are always encrypted by the public key of the recipient certificate, as follows:
- A request from the client to the virtual service is encrypted by the virtual service's certificate.
- A request from the virtual service to the real service is encrypted by the real service's certificate.
- A response from the real service to the virtual service is encrypted by the virtual service's certificate.
- A response from the virtual service to the client is encrypted by the client's certificate. The client is identified by the UsernameToken security header in the initial request. Mapping the client’s certificate to its user name in the OpenText Service Virtualization credential store enables OpenText Service Virtualization to choose the correct client certificate for encrypting the response.
Set security for an encrypted request and response
- In the Virtual Service Editor, expand Security Settings.
-
Click Edit Credential Store, and create identities as follows:
- Client certificate: Username must match the username in the UsernameToken of the request.
- Virtual service certificate with private key.
-
Real service certificate with public key.
Note: If you have the real service certificate's private key, you can use it as the Virtual Service Identity and do not need an additional certificate for the virtual service.
Example:
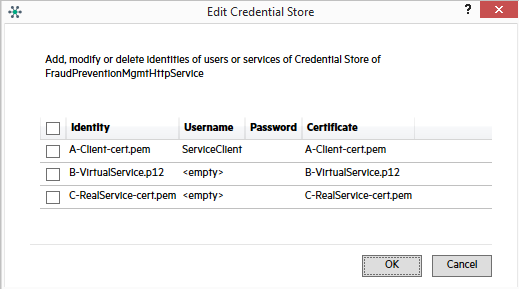
-
Under Message Security, fill in the relevant fields.
Example:
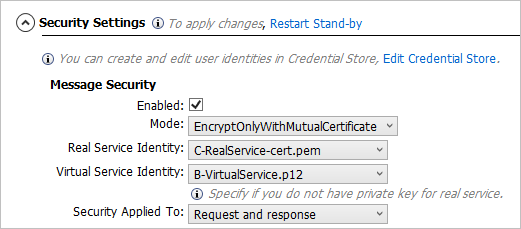
Set security for an encrypted request only
The settings are the same as above, with two exceptions:
- The client username and certificate are not required in the credential store.
- Under Message Security, set the Security Applied To field to Request only.
-
Example:
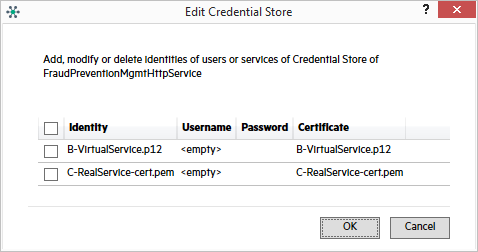
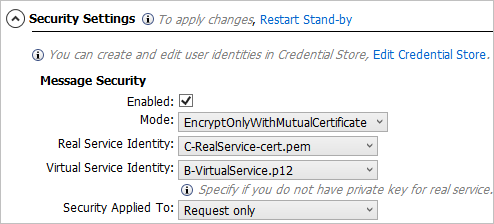
Configure SupportingCertificateOverTransport mode
Supporting certificate over transport mode uses a supporting binary token over HTTPS:
-
Transport security binding
-
Algorithm suite: Basic256
-
Layout: Strict
-
-
Endorsing supporting token
-
X509Token (WssX509V3Token10) always included to recipient
-
Inclusion type: MustSupportRefThumbprint / RequireThumbprintReference
-
To configureSupportingCertificateOverTransport mode:
-
Prerequisites:
- You must have created a virtual service.
- The OpenText Service Virtualization Credential Store must contain an identity with each used client certificate.
- In the Virtual Service Editor, expand Security Settings. Under Message Security, select Enabled.
-
In the Mode drop-down box, select SupportingCertificateOverTransport.
Note:
- Do not configure Real Service Identity or Virtual Service Identity.
- This mode does not support advanced configuration.
Configure UserNameOverTransport mode
User name over transport mode uses a signed supporting user name token over HTTPS:
-
Transport security binding
- Algorithm suite: Basic256
-
Layout depends on WS-Security version configured in Advanced settings:
-
WS-Security 1.0: Lax
- WS-Security 1.1: Strict
-
-
Endorsing supporting token
-
UserNameToken (WssUsernameToken10) always included to recipient.
Only PasswordText token type is supported.
-
To configure UserNameOverTransport mode:
-
Prerequisites:
- You must have created a virtual service.
- The OpenText Service Virtualization Credential Store must contain an identity with each user and password used for authentication to the real service.
- In the Virtual Service Editor, expand Security Settings. Under Message Security, select Enabled.
-
In the Mode drop-down box, select UserNameOverTransport.
Note: Do not configure Real Service Identity or Virtual Service Identity
-
Click Advanced Settings to open the Advanced Message Security Settings dialog box, and configure as follows:
- Protection Level. This setting has no effect because encryption and signing are provided by the transport level (HTTPS).
- Message Protection Order. This setting has no effect because encryption and signing are provided by the transport level (HTTPS).
-
Message Security Version. Layout used for security header:
- Message security versions using WS-Security 1.0 use Lax layout for security header.
- Message security versions using WS-Security 1.1 use Strict layout for security header.
- Require Derived Keys. This setting has no effect.
- Include Timestamp. This setting controls if requests and responses must contain a security timestamp.
- Allow Serialized Signing Token on Reply. This setting has no effect.










