Configure secured JMS
This topic describes how to configured secured JMS if you are using a Tibco EMS SSL connection.
Server-side configuration
On your secured JMS server machine:
-
Obtain any certificates required from your server administrator. For example, you may need files similar to the following:
- server_root.cert.pem
- client_identity.cert.pem
- server_root.cert.pem
- server.cert.pem
- server.key.pem
- client_root.cert.pem
-
Locate and open the factories.conf file for editing. This file is located in the server installation directory.
-
In the factories.conf file, define your JMSConnectionFactory settings.
Define the following:
- type = queue
- url = the binding SSL URL
- ssl_trusted = the path to the server-side certificate
- ssl_verify_host = false
For example
[JMSConnectionFactory]
type = queue
url = ssl://localhost:7243
ssl_trusted = C:\...\server_root.cert.pem
ssl_verify_host = false
-
Continue editing the factories.conf file to create the direct SSL factory.
Define the following:
- ssl_identity = the path to the client-side certificate
- ssl_trusted = the path to the server-side certificate
For example:
[SSLQueueConnectionFactory]
type = queue
url = ssl://localhost:7243
ssl_identity = C:\...\client_identity.cert.pem
ssl_trusted = C:\...\server_root.cert.pem
-
Locate and open the tibemsd.conf file for editing. This file is located in the server installation directory.
-
In the tibemsd.conf file, define the following values:
- authorization = enabled
- listen = the binding SSL URL
- track_message_ids = enabled
- ssl_server_identity = the path to the server-side certificate
- ssl_server_key = the path to the server-side key
- ssl_password = the password associated with the server-side key
- ssl_server_trusted = the path to the client certificate
For example:
authorization = enabled
listen = ssl://localhost:7243
track_message_ids = enabled
ssl_server_identity = C:\...\server.cert.pem
ssl_server_key = C:\...\server.key.pem
ssl_password = ***
ssl_server_trusted =C:\...\client_root.cert.pem
-
Configure a user and group on the server side:
- Launch the Start EMS Administration tool and log in.
- Create a group, and add your user to the new group.
- Grant the new group privileges to access the queue.
For example, after logging in, run the following commands:
create group securegroup
add member securegroup admin
grant queue inQueue group=securegroup send
grant queue inQueue group=securegroup receive
grant queue inQueue group=securegroup browse
Client-side configuration
On your OpenText Functional Testing machine:
-
Copy any relevant .jar files from the EMS server machine to the OpenText Functional Testing machine.
-
Edit your Test Settings values. For example:
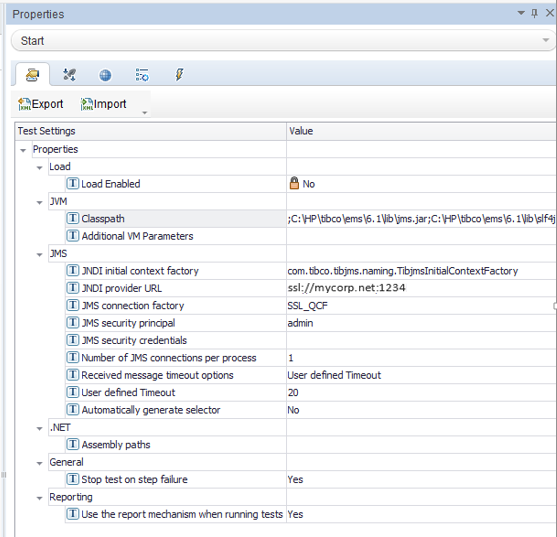
In this example, the Classpath value is set to:
C:\HP\tibco\ems\6.1\lib\jms.jar;C:\HP\tibco\ems\6.1\lib\slf4j-api-1.4.2.jar;C:\HP\tibco\ems\6.1\lib\slf4j-simple-1.4.2.jar;C:\HP\tibco\ems\6.1\lib\tibcrypt.jar;C:\HP\tibco\ems\6.1\lib\tibemsd_sec.jar;C:\HP\tibco\ems\6.1\lib\tibjms.jar;C:\HP\tibco\ems\6.1\lib\tibjmsadmin.jar;C:\HP\tibco\ems\6.1\lib\tibjmsapps.jar;C:\HP\tibco\ems\6.1\lib\tibjmsufo.jar;C:\HP\tibco\ems\6.1\lib\tibrvjms.jar
For more details, see Test Settings Tab (Properties Pane - API Testing).












