You can configure your LoadRunner Professional environment to communicate with two-way TLS (SSL) authentication. In this mode, the server sends its own certificate and requests from the client to send it a client certificate for validation.
Configurations for two-way TLS authentication
The following images illustrate some possible configurations when using two-way TLS authentication:
-
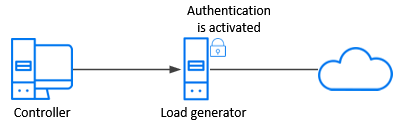
Controller—load generator communication. In this environment, the load generator machine is the server and Controller is the client. You activate authentication on the load generator, enforcing secure communication between the machines.
-
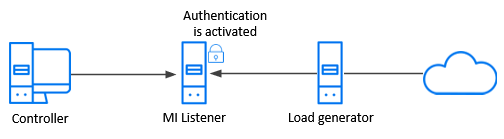
Controller—load generator—MI Listener communication. In this over-firewall environment, the MI Listener machine is the server, and Controller and load generators are the clients. You activate authentication on the MI Listener machine which, in turn, enforces secure communication with the Controller and load generators.
-
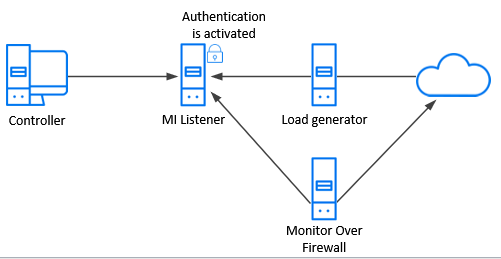
Controller—MI Listener—load generator—Monitor Over Firewall Communication. In this over-firewall environment, the MI Listener machine is the server. The Monitor Over Firewall, Controller, and load generator machines are the clients. You activate authentication on the MI Listener machine which, in turn, enforces secure communication with the other machines.
Configure two-way TLS (SSL) authentication
The following procedure describes the steps required to set up secure communication with two-way TLS (SSL) authentication in your LoadRunner Professional environment.
To set up two-way TLS authentication:
-
Set up the CA and TLS certificates
- Create a Certificate Authority (CA) certificate or ensure that you have a valid existing CA certificate, as well as any required intermediate CA certificates.
-
Create or select a TLS certificate.
-
Install the CA certificate, intermediate CA certificates (if required), and the TLS certificate on all relevant LoadRunner Professional machines in your system.
For details, see Certificate Manager.
-
Determine which machine in your system is the server for client-server communications.
-
Activate client authentication on the machine acting as the server.
Do one of the following:
- Use the Network and Security Manager command line tool to activate authentication for the host machine that is acting as the server. Set -check_client_cert to 1.
-
When working over a firewall, in the Agent Configuration Over Firewall Settings Dialog Box, select Use Secure Connection (SSL) and enter relevant details.
-
Configure authentication settings in Controller.
In Controller, select the CA and TLS certificates to be used for the scenario run. For details, see Certificate Manager.
-
Activate server authentication on client machines (optional).
If you want the client machines to validate the server certificate, set this option for each client machine.
Do one of the following:
- Use the following Network and Security Manager command line from a single location to activate server authentication on all relevant host machines: set -check_server_cert to High for the highest level of security. For more information, see -check_server_cert.
- On each client machine in your system, enable the Use Secure Connection (SSL) option in the Agent Configuration Settings dialog box, and set the Check Server Certificates level.
Note: When provisioning load generators on the cloud, the certificates are taken from Controller and automatically copied to the load generators, so the communication is secure by default. For details about working with load generators on the cloud, see Load generators on the cloud.












