SAML SSO settings
In the Administration settings > SAML SSO integration tab, you can enable single-sign-on (SSO) to Digital Lab. This way, users can use one set of credentials for logging into Digital Lab, as they do for logging into other SSO applications in their organization. This section is relevant only for UFT Digital Lab and UFT Digital Lab Manged SaaS.
Note: When configuring Digital Lab to work with SAML SSO, the connection to the Digital Lab must be over SSL. For details, see Windows Installation or Linux Installation.
Set up the SAML SSO integration
Digital Lab supports single-sign on via SAML 2.0. SAML (Security Assertion Markup Language) is an XML-based standard for exchanging authentication and authorization data between an identity provider (IdP) and a service provider, such as Digital Lab.
To enable SAML SSO integration, you need to add Digital Lab to your Identity Provider (IdP). Refer to your Identity Provider documentation for instructions on how to configure your IdP for a new SAML 2.0 application. You need information (metadata) about Digital Lab when configuring your IdP. Download this by clicking the DOWNLOAD Digital Lab METADATA link.
You also need to add the following information from your IdP to Digital Lab, so that SAML-based authentication requests can be sent to your IdP:
| IdP SAML metadata |
This can be a URL, or you can copy and paste the contents of the IdP metadata .xml file into this field. |
| Administrator login name |
This is a user, defined in the IdP, that is granted Digital Lab administrator permissions. Initially, only this user is able to access the Administration menu |
| Username attribute identifier |
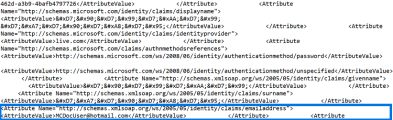
User attributes are information used to identify individual users. In this field, provide the SAML attribute name for the username attribute that the IdP uses for identification on sign in. Depending on how you configured your IdP, the username attribute for signing in can be an email address, or a unique user name. Tip: Find the attribute identifier in the AttributeStatement section of the IdP SAML response. Look for the SAML attribute name with a value that equals the attribute that IdP uses for identification on sign in. For example, if email address is used for authentication of users against the IdP, the identifier in the example below is http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress Alternatively, use {$id} to take the username from the subject of the SAML assertion, and not from Attribute section. |
After you have successfully defined the SSO settings, you are prompted to log out and to log in again using your organization credentials.
Update settings
You can update the SSO integration settings if needed. When you update any of the settings, you are prompted to log out and to log in again using your organization credentials. If you disable SAML SSO, you need to use your Digital Lab credentials to log in again.
Note: When you enable or disable the SSO setting, all existing users, excluding admin@default.com, are deleted.
If you enabled SSO but cannot log in to Digital Lab as an administrator, for example, if you wrongly configured the administrator user, you can disable SAML SSO by running the User management script.
Note for Digital Lab SaaS: The IdP must be accessible over the internet. Add the Digital Lab SaaS address to your allowlist if needed.
 See also:
See also:






 to perform administration tasks such as configuring settings, and managing workspaces, licenses, and access keys. The administrator can assign admin permissions to additional users by changing the user role in Administration > Settings > Users.
to perform administration tasks such as configuring settings, and managing workspaces, licenses, and access keys. The administrator can assign admin permissions to additional users by changing the user role in Administration > Settings > Users.